Access Control and Surveillance as IP Infrastructure
Access Control and Surveillance as IP Infrastructure
Devices and Applications in the corporate environment have become increasingly IP-based. The IP which used to be always there on the backend, at the integration level, is finding a place in front end user application as well. The simplicity and familiarity to configure are the two main reasons which drive the IP adoption.
The recent two new applications, which were traditionally non-IP or non-IT, are access control and surveillance, to be added to IP Infrastructure. Both these applications are beside whatever have already transformed like voice communication (SIP Now), Storages, Wireless access etc. Access control and Surveillance, both these devices used IPs; only in the head-end side where the storage media or controllers are connected to the network infrastructure. Today CCTV cameras and the access controller up to the sensor level, are IP enabled and ready for deployment as part of the IT infrastructure.
These changes have been gradually happening for the last 10 years. Because of the ubiquitous nature of IP in the infrastructure, it is logical for any manufacturer to adopt IP for their applications to be part of the infrastructure. All the Low voltage applications, including the Industrial Automation, will morph or change to IP Infrastructure

From Ad-Hoc to Audit-Ready: Modernizing Legacy Manufacturing Networks in India (IT + OT + Compliance)
Many manufacturing networks in India evolved organically over the years—one unmanaged switch added for a new production line, a Wi-Fi router dropped in for the warehouse, and a few “patch-and-go” fixes to keep downtime low. While these decisions made sense at the...
IoT / OT/ Industrial Firewalls vs Enterprise Firewalls
For a very long, the firewall was a singular concept. Placed at edge of a network, inspected packets, blocked suspicious traffic, and allowed business applications to function. Whether protecting a corporate LAN, data center, or branch office, the same category of...
Data Control with Captive Portal & Firewall
In many businesses, providing internet access to guests, customers, or temporary users is necessary — but giving them unrestricted data can quickly lead to abuse, bandwidth congestion, and security issues.Whether you're running a café, coworking space, hotel, school,...
Supermicro DCBBS: Liquid-Cooled, Modular AI Infrastructure for Scalable Performance
Supermicro’s DCBBS: A Novel and Smart-Way to Keep AI Liquid and Data-Reaching Shelves Flat and Cool. While artificial intelligence (AI), high-performance computing (HPC), and data-intense workloads are transforming industries, traditional data centers are facing...
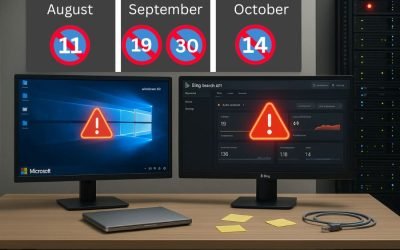
Microsoft Products Reaching End of Support (Aug–Oct 2025): Key Dates, Risks & What to Do Now
Microsoft Products End of Support in August–October 2025: What You Need to Know & Do Now As we draw close to the last quarter of 2025, we have several key services and products from Microsoft that are either retiring or reaching End of Support (EOS). From APIs and...
Why Should you Care About the Energy Efficiency of APs Like MR44?
As enterprises grow increasingly reliant on wireless infrastructure, the energy demands of networking hardware have become a significant factor in IT operations. Among modern wireless solutions, the Cisco Meraki MR44 access point stands out due to its performance...
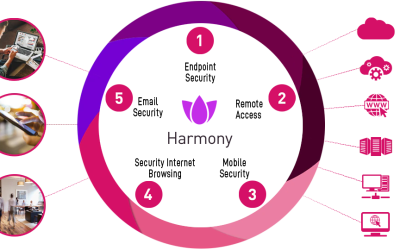
How Checkpoint Harmony Defends Your Digital Inbox
Email has been the cornerstone of business communication for decades. It’s fast, flexible and accessible. But it’s also the most exploited entry point for cyberattacks. Today cybercriminals don’t need to hack firewalls to enter the network they just need one employee...
Understanding Proximity Detection in Meraki Access Points
Businesses are increasingly using technology to improve services, security and overall network performance. One such technology is proximity detection in Meraki Access Points (APs), which helps track devices within their coverage area. This feature provides valuable...
MCS8 and MCS9: Which is better for your WiFi needs?
A very common feature of Access Points from leading brands like Aruba, Cisco Meraki, and Ruckus is support for MCS8 and MCS9, which are modulation and coding schemes widely used in the devices complying to modern Wi-Fi standards. Some of the Series from Aruba are...
Bluetooth Low Energy (BLE) in WiFi Devices: Why does it matter?
Bluetooth Low Energy (BLE) is a wireless communication technology for low-power devices in short range. It is widely used in smart devices, to enhance connectivity and energy efficiency. How does BLE work? BLE (Bluetooth Low Energy) operates in the 2.4 GHz ISM...