CYBERSECURITY SOLUTIONS
Are you seeking comprehensive Cybersecurity solutions for your SMB or Enterprise?
Search no more! We have over 27 years of experience and a strong commitment to customer satisfaction. Reach out to us today to discover how we can secure your IT systems

Why Cybersecurity solutions?
The threat landscape of any Organization is rapidly evolving and the cyber attacks are increasingly concerted, collaborative and sophisticated. The organisations have to strategise suitable defensive mechanisms to protect their Valuable assets. Gone are the days where the forms of Denial of Services or availability of applications were the most sophisticated attacks. Gone are the days where the attacks were executed by smart individuals to prove their skills or hired agencies to bring down a website or a mail server. The modern threat actors are well endowed; sometimes even State sponsored.
Also compliance requirements of GDPR or Digital Personal Data Protection Act of India (DPDP), 2023 needs very robust Policies and tools to prevent unintentional loss of PIIs if the consent is withdrawn.
Cybersecurity solutions are important for the enterprises to protect sensitive data, adhere to compliance and ensure business continuity.
There are several point solutions when it comes to securing your IT assets. Therefore cybersecurity solution must be mutli-layered, for example; Implementing Identity and Access Management (IAM) prevents unauthorized access, while Endpoint Detection and Response (EDR) helps identify and mitigate threats in real-time. Multi-Factor Authentication (MFA) adds an extra layer of security..
By leveraging advanced cybersecurity solutions, enterprises can proactively defend against cyber threats and ensure excellent protection for their digital assets.
User & Device Management
User and device management are integral to cybersecurity, ensuring only authorized individuals and devices access corporate resources. Identity and Access Management (IAM) systems control user permissions, reducing the risk of insider threats. Mobile Device Management (MDM) solutions secure and monitor mobile devices, protecting data even if a device is lost or stolen. Apple’s MDM, for instance, enforces encryption and remote wipe capabilities.
Together, these solutions maintain a secure, compliant, and efficient IT environment, mitigating risks from unauthorized access and compromised devices.

Identity & Access Managment (IAM)
IAM (Identity & Access Mannagement) give secure access to the company emails, database, and application, and it helps to ensure the right person have the access to the technology resources. With the help of IAM system, the organisation can quickly and accurately verify person’s identity.
.

Mobile Device Management (MDM)
Mobile Device Management (MDM) is a solution designed to securely manage and control mobile devices, within an organization’s network. MDM involves configuring settings, enforcing security measures, and remotely monitoring and troubleshooting devices.

Multi-Factor Authentication (MFA)
It is a multi-step authentication process that required users to enter more details than just a password. It helps to prevent unauthorised access if the password has been encrypted. It helps to minimise threats and human errors .

Single Sign-On (SSO)
It is an authentication method with one set credential it helps to access multiple application and website. This simplifies the user experience by reducing the need to remember multiple passwords and enhances security by centralizing authentication.
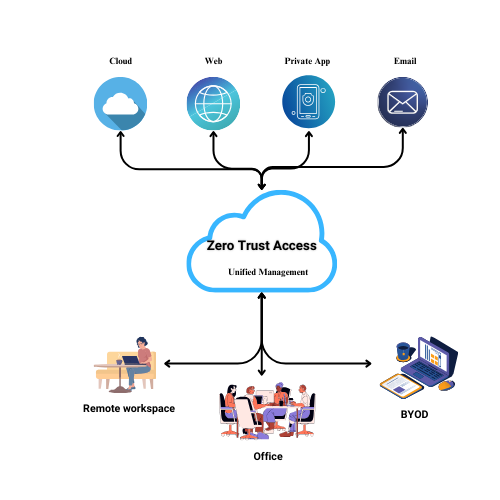
ZTNA (Zero Trust Network Access)
Before ZTNA (Zero Trust Network Access) implementation, traditional security relied on VPNs (Virtual Private Networks), which provided broad network access based on location. Users were expected to be trustworthy within the network perimeter, which presented potential risk.
ZTNA (Zero Trust Network Access) ensures detailed access, based on user identification and context, eliminating dependency on a static perimeter while offering flexible, secure connectivity to users working from anywhere.
We at Vays, specialize in offering ZTNA as a service to provide cloud-based solutions that organizations can subscribe to, eliminating the need for extensive infrastructure investments.
Threat Detection and Response
Threat detection and response are pivotal in cybersecurity, enabling organizations to identify and mitigate cyber threats swiftly. Extended Detection and Response (XDR) solutions, provide a unified approach to detect threats across multiple environments. Endpoint Detection and Response (EDR), focuses on identifying and responding to threats at the device level. Managed Detection and Response (MDR) services, combine advanced tools with expert analysis for 24/7 monitoring. These solutions ensure comprehensive protection by detecting anomalies, responding to incidents, and minimizing potential damage from cyber attacks.

Endpoint Detection and Response (EDR)
EDR focuses exclusively on monitoring and responding to threats on endpoint devices such as computers, servers, and mobile devices.
It provides visibility and control primarily at the endpoint level, analysing endpoint activities, processes, and behaviours to detect and respond to threats.
They offer endpoint-centric threat detection and response capabilities, with a focus on endpoint security
.

Extended Detection and Response (XDR)
XDR expands beyond endpoint devices to encompass multiple security layers, including network, email, cloud, and more.
It integrates data from various sources to provide a broader view of the organization’s security posture and enables the correlation of threats across different layers of the IT environment.
XDR solutions typically offer advanced threat detection, investigation, and response capabilities across multiple security domains.

Managed Detection and Response (MDR)
MDR services encompass the monitoring, detection, and response to threats across an organization’s entire IT environment, including endpoints, networks, cloud environments, and more.
Their services are focused on providing proactive threat detection and response capabilities, often leveraging security expertise and advanced technologies to detect and respond to threats in real-time.

Cloud Detection and Response (CDR)
CDR stands for Cloud Detection and Response. It’s a cybersecurity solution that focuses on monitoring and responding to threats within cloud environments, such as cloud-based applications, platforms, and infrastructure.
CDR solutions offer visibility and control over cloud-based activities and resources, analysing data and behaviours to detect and respond to security incidents.
Microsoft Solutions
Microsoft Windows offers robust cybersecurity through advanced threat protection, identity management, and information protection. Collaboration with Vays enhances these frameworks, providing enterprises with more comprehensive and integrated security solutions.

Microsoft Azure Actuve Directory / Entra ID
It helps to Safeguard organization with a cloud identity and access management solution that connects employees, customers, and partners to their apps, devices, and data.
- Secure adaptive access
Protect access to resources and data using strong authentication and risk-based adaptive access policies without compromising user experience.
- Seamless user experiences
Provide a fast, easy sign-in experience across your multicloud environment to keep your users productive, reduce time managing passwords, and increase productivity.
- Unified identity management
Manage all your identities and access to all your applications in a central location, whether they’re in the cloud or on-premises, to improve visibility and control.
Microsoft Entra ID empowers organizations to manage and secure identities so employees, partners, and customers can access the applications and services they need. Microsoft Entra ID provides an identity solution that integrates broadly, from on-premises legacy apps to thousands of top software-as-a-service (SaaS) application, delivering a seamless end-user experience and improved visibility and control.

Microsoft Intune
Microsoft Intune is a cloud-based endpoint management solution. It manages user access to organizational resources and simplifies app and device management across your many devices, including mobile devices, desktop computers, and virtual endpoints.
Organization-owned devices are managed with Intune for mobile device management (MDM). MDM focuses on the device, so features are set up based on user needs. For example, a device can be configured to allow Wi-Fi access only for organization accounts.
In Intune, you create policies to set up features, settings, and security. The admin team manages the devices, user identities, apps, and data access. Policies are deployed during device enrollment, so once enrollment is complete, the device is ready to use.
For personal devices or bring-your-own-device (BYOD) setup, Intune uses mobile application management (MAM). MAM protects app data no matter the device. It focuses on securing apps and their data.
With MAM, you can:
- Publish and update mobile apps for users
- Configure apps automatically
- View reports on app usage and inventory

Azure Firewall
Azure Web Application Firewall is a cloud-native service that protects web apps from common web-hacking techniques such as SQL injection and security vulnerabilities such as cross-site scripting. Deploy the service in minutes to get complete visibility into your environment and block malicious attacks.
- Custom and managed rule sets to prevent malicious attacks at the edge
- Real-time visibility into your environment and security alerts
- Full REST API support to automate DevOps processes

Windows Defender
Defender for Business helps you to identify, protect against, detect, and respond to sophisticated cyberattacks, helping you to stay secure.
- Improve visibility and response time to attacks with endpoint detection and response.
- Identify and stops emerging threats with next generation antivirus protection.
- Continuously protects your business from malicious activity through automated investigation and remediation.
- Track vulnerabilities across your most critical assets.
Crowdstrike Solutions
As a Crowdstrike partner we at Vays offer a comprehensive suite of products and solutions designed to keep your business safe from cyber threats.

Crowdstrike Falcon Insight XDR (Endpoint Detection & Response)
Strong responsiveness and endpoint protection features are provided by this platform. It gives enterprises visibility into endpoint activities, assisting in identifying and handling security events.
Crowdstrike Falcon Prevents (Next Generation Antivirus)
Falcon Prevent provides enhanced security by proactively blocking cyberattacks with the use of cutting-edge technology like machine learning. It goes beyond conventional antivirus software by adjusting in real-time and offering dynamic, efficient endpoint protection
Falcon Intelligence (Threat Intelligence)
A threat intelligence service called Falcon Intelligence by CrowdStrike gives businesses up-to-date knowledge on cybersecurity threats so they may take preventative action. By utilizing cutting-edge analytics, it improves overall cybersecurity resilience by assisting in the identification and mitigation of new threats.
