DATA SECURITY
Are you seeking comprehensive Data Security services for your SMB or Enterprise?
Search no more! We have over 25 years of experience and a strong commitment to customer satisfaction. We are here to help you succeed. Reach out to us today to discover how we can support your security landscape


Why is Data Security important?
Data security is important for enterprises due to several key factors. Firstly, ensuring confidentiality by protecting sensitive information such as intellectual property, customer data, PII (personally identifiable information) and financial records from unauthorized access and breaches. Effective Compliance with regulations like DPDP Act of India, GDPR is non-negotiable; failing to meet these standards can result in substantial fines and legal repercussions.
Moreover, threat mitigation strategies are essential to defend against sophisticated cyberattacks, ransomware, and data leaks. Finally, resilience in data security ensures that your business can maintain operational continuity and quickly recover from incidents.
In the current threat landscape, an efficient data security framework isn’t just a protective measure—it’s a strategic imperative. Investing in comprehensive encryption, access control, IDPS, and backup solutions is critical. Immediate action to strengthen these areas will not only safeguard your enterprise’s assets but also reinforce stakeholder trust and compliance posture.
DATA CLASSIFICATION
Data classification involves categorizing data based on its sensitivity and value. This technique ensures that the most critical data receives the strongest protection measures, aids in regulatory compliance, and optimizes security resource allocation, enhancing overall data security.

DATA ENCRYPTION
Data encryption converts data into a coded format to prevent unauthorized access. This technique protects data at rest and in transit, ensuring confidentiality and integrity, thereby safeguarding sensitive information from breaches and enhancing overall security.

DATA LOSS PREVENTION (DLP)
Data Loss Prevention (DLP) identifies, monitors, and protects sensitive data from unauthorized access, transfer, or leaks. This technique ensures that critical information remains secure within the organization, preventing data breaches, and aiding compliance with regulatory requirements.

ACCESS CONTROL
Access controls regulate who can view or use resources in a computing environment. By implementing authentication and authorization mechanisms, this technique ensures that only authorized users can access sensitive data, reducing the risk of data breaches and insider threats.
Solution Partners






Data Security Posture Management (DSPM)
Data Security Posture Management (DSPM) is a vital part of new-age data security strategies, offering extensive visibility and control over data security across cloud and on-premises environments.
DSPM includes comprehensive data discovery and classification, continuous monitoring for anomalies, automated policy enforcement with encryption, risk assessment, and integration with other security solutions, ensuring data protection and quick incident response.
- Data Discovery
- Data Classification
- Real time monitoring
- Vulnerability scanning
- Risk Remediation
We provide DSPM solutions and services customized to the unique needs of your enterprise. Our advanced tools and expertise ensure seamless integration, continuous monitoring, and policy enforcement, enhancing your data security posture.
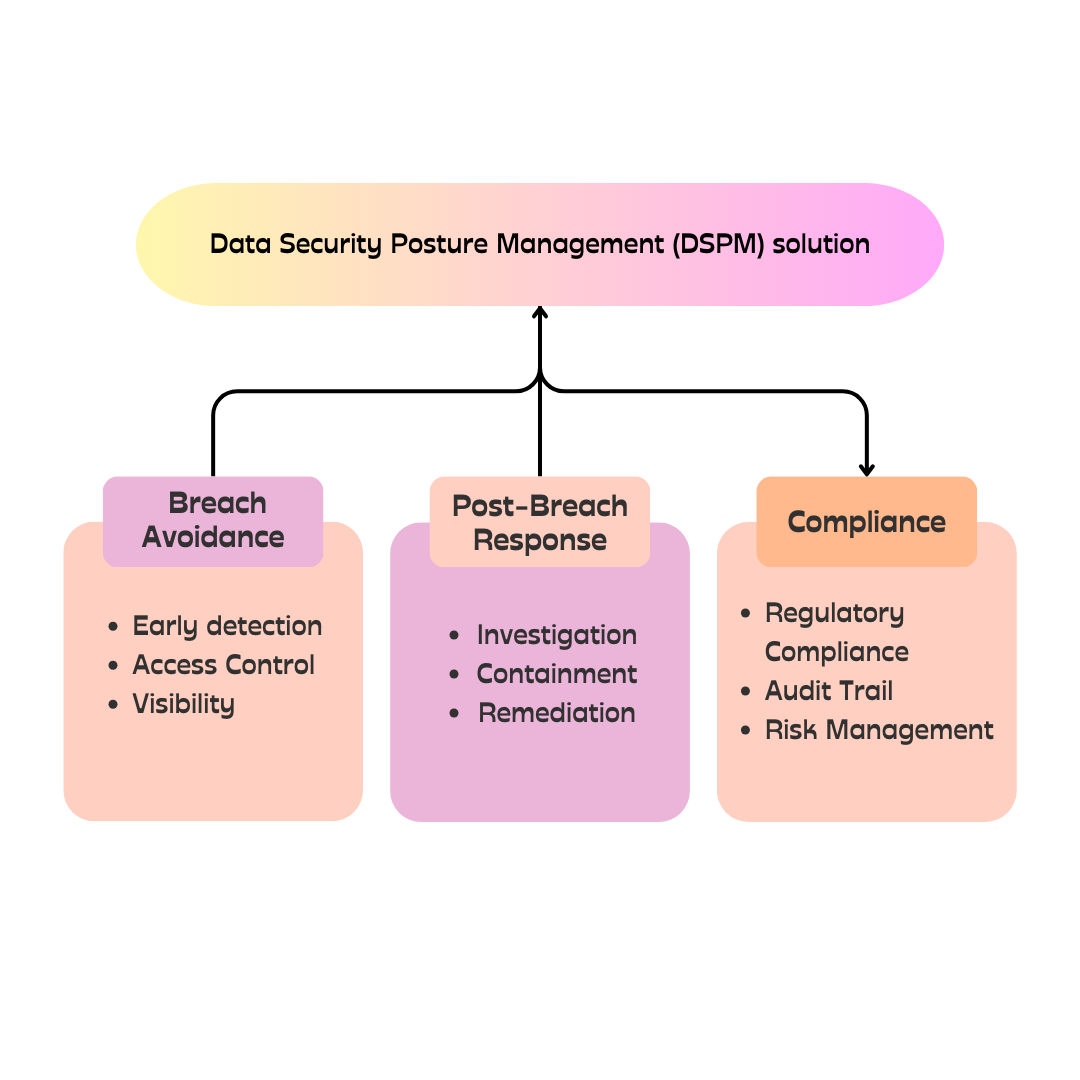
Complete Data Visibility
- Provides a unified view of data assets and their security status across diverse environments.
- Helps identify and categorize sensitive data, ensuring proper protection measures are applied.
Proactive Risk Management
- Continuously assesses security configurations and practices to identify potential vulnerabilities.
- Enables proactive remediation efforts to address risks before they lead to breaches.
Regulatory Compliance
- Ensures adherence to legal and regulatory requirements such as GDPR, DPDP Act, and more
- Avoids substantial fines and legal repercussions associated with non-compliance.
Varonis Solutions
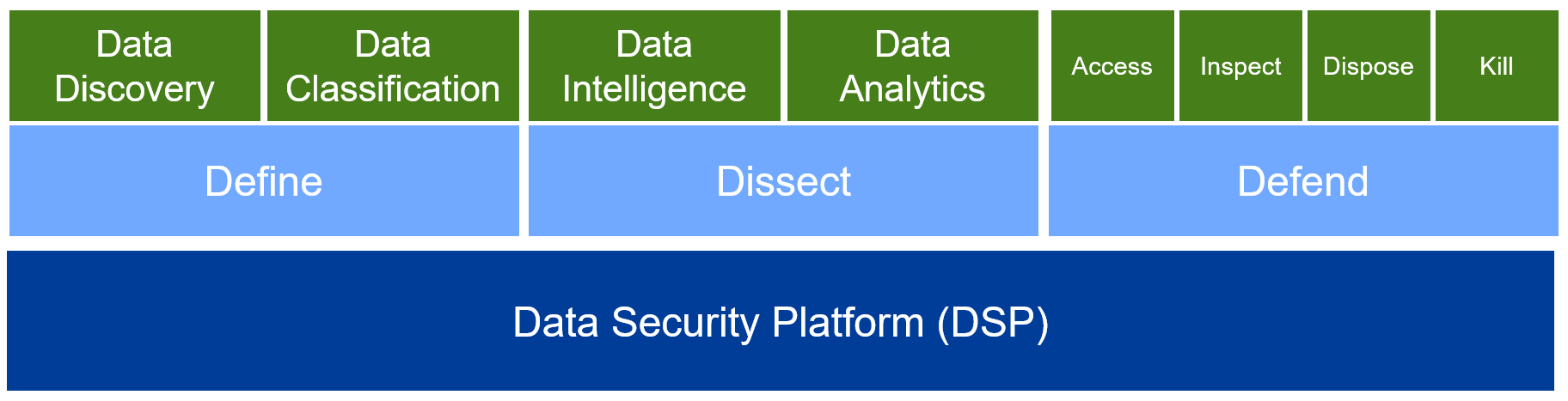
Varonis Data Security Platform
- Data Discovery and Classification: Automatically discovers and classifies sensitive data across file systems, email systems, and cloud storage.
- Permissions Management: Analyzes and manages permissions to ensure only authorized users have access to sensitive data.
- User Behavior Analytics (UBA): Monitors user activity and detects anomalous behavior indicative of insider threats or compromised accounts.
- Alerting and Reporting: Provides real-time alerts and comprehensive reports on data access and usage.
- Incident Response: Facilitates rapid investigation and response to security incidents.
The Varonis Data Security Platform solves the data threat issues in the following ways:
- Identifies and protects sensitive data from unauthorized access.
- Prevents data breaches by monitoring and controlling data access.
- Detects and mitigates insider threats and compromised accounts.
- Ensures compliance with data protection regulations.

Varonis provides a suite of data security and analytics solutions designed to protect enterprise data from insider threats, data breaches, and cyberattacks. By teaming up with Vays Infotech a leading IT Service and consulting provider, you can harness the complete capabilities of Varonis solutions and optimize their effectiveness throughout the enterprise
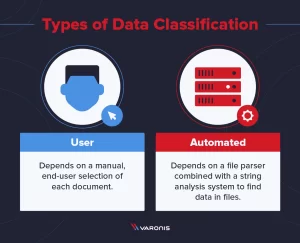
Data Classification Engine
- Automated Classification: Uses machine learning to classify sensitive data based on content and context.
- Policy Enforcement: Applies policies to protect classified data, such as encryption and access restrictions.
- Comprehensive Coverage: Supports a wide range of data repositories, including on-premises and cloud environments.
- Detailed Reporting: Generates reports on data classification status and policy compliance.
Data Loss Prevention (DLP)
Data Loss Prevention (DLP) is a data security strategy that invovles identifying, monitoring and protecting sensitive data from unauthorized access, transfer, or leaks.
Technically, DLP involves data identification and classification using content inspection and metadata, continuous monitoring for anomalies, and policy enforcement with encryption and access controls. It also integrates with other security measures, such as endpoint protection and network security, to provide comprehensive protection. Additionally, DLP generates alerts and detailed logs for rapid response and forensic analysis, ensuring regulatory compliance and safeguarding the enterprise’s most valuable assets.

Prevention of Data Breaches
- Detects and blocks attempts to transfer sensitive data outside the organization.
- Minimizes the risk of data breaches and insider threats.
Enhanced Visibility and Control
- Provides real-time monitoring and visibility into data movement within the organization.
- Allows for the implementation of policies to control data usage and sharing.
Regulatory Compliance & Data Protection
- Helps meet legal and regulatory requirements such as GDPR, DPDP Act and more
- Avoids substantial fines and legal repercussions associated with non-compliance
Forcepoint Solutions
Forcepoint DLP
- Discovery and Classification: Automatically discover and classify sensitive data across endpoints, networks, and cloud environments.
- Policy Enforcement: Granular policy controls to enforce how data is used, transferred, and stored.
- Incident Management: Detailed incident workflows to manage and respond to data loss incidents.
- User Education: Real-time user prompts to educate and alert users about risky behaviors.
- Contextual Intelligence: Advanced analytics to understand the context of data usage and identify potential risks.
- Integration: Seamless integration with other Forcepoint products and third-party solutions.

By teaming up with Vays Infotech a leading IT Service and consulting provider, you can harness the complete capabilities of Forcepoint’s solutions and optimize their effectiveness throughout the enterprise

Insider Threat
- Monitoring and analysis of user activity.
- Detection of anomalous behavior and insider threats.
- Risk scoring and automated response
- Protects against data theft and sabotage by internal users.

Email Security
- Advanced threat detection and phishing protection.
- Data loss prevention for email communications.
- Spam filtering and email encryption.
- Detailed reporting and analytics
- Prevents email-based attacks, including phishing and malware.
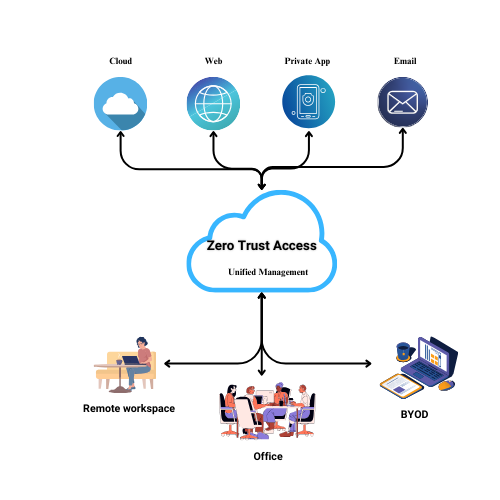
ZTNA (Zero Trust Network Access)
Before ZTNA (Zero Trust Network Access) implementation, traditional security relied on VPNs (Virtual Private Networks), which provided broad network access based on location. Users were expected to be trustworthy within the network perimeter, which presented potential risk.
ZTNA (Zero Trust Network Access) ensures detailed access, based on user identification and context, eliminating dependency on a static perimeter while offering flexible, secure connectivity to users working from anywhere.
We at Vays, specialize in offering ZTNA as a service to provide cloud-based solutions that organizations can subscribe to, eliminating the need for extensive infrastructure investments.
Why Vays?
At Vays, we specialize in delivering an extensive range of Security Managed Services across major cities in India. Our focus areas include network security, firewall management, and cybersecurity.
Our offerings comprehensively cover the protection of networks, operating systems, data, applications, and cloud environments. With meticulous attention to detail, we actively ensure that businesses have up-to-date security measures in place to safeguard their critical assets from cyber threats and vulnerabilities.
Our dedicated team takes pride in providing a human touch to our services, prioritizing the specific needs and concerns of each client.


Customized Solutions
Every business is unique, and so are its data security needs. Recognizing this, we don’t believe in a one-size-fits-all approach. Instead, we take the time to understand your specific business operations, infrastructure, and potential threats to provide a customized security solution.

Employee Training
We equip your team with the necessary knowledge to maintain network security and react to potential threats. This includes teaching them best practices for secure use, and showing them how to respond effectively in case of a potential security incident.

Save costs
Our cybersecurity professionals provide businesses with specialized skills and knowledge, allowing them to focus on their core operations. This enhances overall productivity and efficiency. With our dedicated professionals safeguarding networks and systems and applications businesses can confidently pursue success.

Expertise
Our team’s deep knowledge in security solutions ensures maximum protection. Our professionals possess specialized skills and knowledge, enabling businesses to prioritize core operations. This strategic approach enhances productivity and efficiency as dedicated experts handle critical security aspects
Partner with Vays
With over 27 years of experience in the industry, we specialize in network security, cybersecurity and data security solutions. As trusted partners, we offer a comprehensive suite of managed services, including on-site assistance and expert technical support. Our skilled engineers are available to assist businesses with seamless imaplementations, installations, updates, and configurations, ensuring they have access to the latest tools and technologies.
At our company, we take pride in our partnerships with competitive firewall brands such as Palo Alto, Varonis, Forcepoint, Fortinet, and more. These collaborations enable us to deliver top-notch security solutions designed to meet the unique needs of each business. Our team is committed to empowering organizations to maintain high-performing and reliable IT infrastructures.
Contact us today for a consultation and let our experts deliver a solution that meets your specific requirements.
Latest News
New customizable tabs put you back in control so that you can see what’s new at a glance and decide which emails you want to read and when.
From Ad-Hoc to Audit-Ready: Modernizing Legacy Manufacturing Networks in India (IT + OT + Compliance)
Many manufacturing networks in India evolved organically over the years—one unmanaged switch added for a new production line, a Wi-Fi router dropped in for the warehouse, and a few “patch-and-go” fixes to keep downtime low. While these decisions made sense at the...
IoT / OT/ Industrial Firewalls vs Enterprise Firewalls
For a very long, the firewall was a singular concept. Placed at edge of a network, inspected packets, blocked suspicious traffic, and allowed business applications to function. Whether protecting a corporate LAN, data center, or branch office, the same category of...
Data Control with Captive Portal & Firewall
In many businesses, providing internet access to guests, customers, or temporary users is necessary — but giving them unrestricted data can quickly lead to abuse, bandwidth congestion, and security issues.Whether you're running a café, coworking space, hotel, school,...



