Insights Worth Exploring – Our Blog
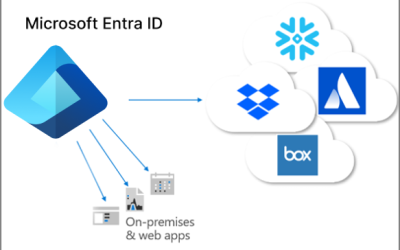
Veeam Backup for Microsoft Entra ID
With the rapid adoption of cloud-based identity management, Microsoft Entra ID (formerly Azure AD) has become a critical component of enterprise IT infrastructure. It serves as the backbone for authentication, access control and identity management. However, relying...
Disaster Recovery challenges in Microsoft Entra ID
Microsoft Entra ID (formerly Azure Active Directory) is a critical identity and access management solution used by enterprises to manage authentication and access control. While it ensures seamless integration with Microsoft 365 and cloud applications, organizations...
A deep dive into HPE Aruba 500 series Access Points
As enterprises rapidly adopt new technologies and embrace growing IoT ecosystems, the demand for reliable, high-performing wireless connectivity has never been greater. Enter the HPE Aruba 500 Series Campus Access Points, designed to revolutionize how organizations...
How to deploy DeepSeek in your office?
What is DeepSeek? DeepSeek is an open-source large language model (LLM) designed for natural language processing (NLP) tasks, similar to OpenAI's ChatGPT. Developed by DeepSeek AI, it aims to provide high-performance AI capabilities with transparency and flexibility,...
Secured Networking using Cisco Meraki Solutions
The essential solutions for a secured networking in an enterprise include: Firewalls: Next-Generation Firewall (NGFW) is an essential component, especially for businesses with remote workers and high security demands. NGFWs provide site-to-site and remote access VPNs...
Cisco Meraki MR44 vs. MR57: Which Access Point is Right for Your Business?
Selecting the right access point is crucial for establishing a fast, secure, and reliable wireless network. Cisco Meraki provides a variety of options, but today we’ll focus on two prominent models—the Meraki MR44 and Meraki MR57. Both models feature advanced...