Email Security Solutions Bangalore
Secure your emails – your first line of defense against adversaries. Emails remain the most exploited entry point for compromising enterprises. At Vays Infotech, with over 27 years of expertise, we deliver advanced, enterprise-grade email security solutions bangalore designed to protect your business from evolving threats.
Phishing Threats Are Evolving — Is Your Business Ready?
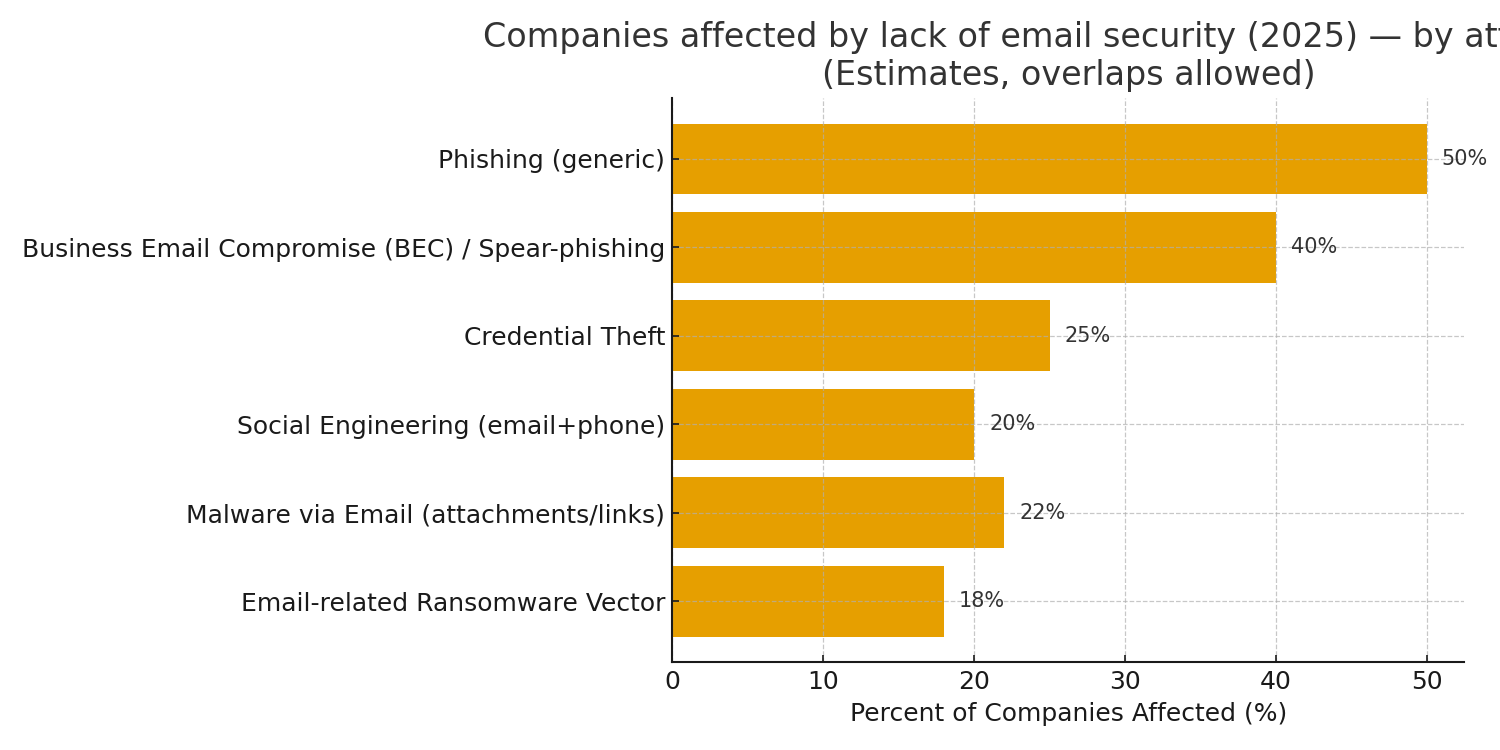
In 2025, email remains the hacker’s top doorway — and weak email security costs businesses dearly. Nearly 50% face phishing, 40% suffer BEC scams, and others fall to credential theft (25%), malware (22%), social engineering (20%), and ransomware (18%).
The damage goes beyond stolen data — it’s financial loss, downtime, and reputational harm. The solution? Advanced filtering, MFA, and employee training. In 2025, email security isn’t optional — it’s survival.
With 27+ Years of Networking & Cybersecurity Expertise
We secure client emails and data with industry-proven solutions from leading providers such as Check Point Harmony, Forcepoint, and Veeam.

Security Solutions for Email

Email Threat Protection
Blocks phishing, ransomware, spam, and malware before they reach inboxes.

Email Authentication
SPF, DKIM, and DMARC enforcement to stop spoofing and protect your domain reputation.

Business Email Compromise (BEC) Protection
Advanced AI detection against CEO fraud, invoice scams, and impersonation attempts.

Email Encryption
End-to-end encryption for sensitive communications in finance, healthcare, legal, and more.

Email Archiving & Continuity
Guaranteed mail access during outages and long-term archiving for compliance and e-discovery.
Data Loss Prevention (DLP)
Stops accidental or intentional leaks of sensitive information.
Harmony Email Security
Email remains the #1 entry point for cyberattacks — from phishing and ransomware to account takeover and data theft. Check Point Harmony Email Security delivers advanced, AI-driven protection to secure your organization’s inboxes and collaboration tools. Leveraging real-time threat intelligence and machine learning, it automatically detects and blocks malicious links, attachments, and impersonation attempts before they reach users.
With robust encryption, policy enforcement, and seamless integration with Microsoft 365, Google Workspace, and other platforms, Harmony ensures that sensitive data stays protected, compliance requirements are met, and teams can collaborate safely without disruption.
Key Capabilities Include:
-
Protects cloud file-sharing services such as Microsoft OneDrive, SharePoint, Google Drive, Dropbox, and Box from malware, ransomware, and malicious links.
-
Dynamic scanning and URL analysis across files ensure threats are blocked before they reach end users.
-
Inline API-based protection reduces phishing emails by 99.2%, with rapid deployment for quick go-live.
-
Part of Check Point Infinity, powered by ThreatCloud — the world’s largest threat intelligence network for real-time, global protection.
Check Point Harmony Email & Collaboration – Key Features
Check Point Harmony is designed to secure email and collaboration platforms like Microsoft 365, Google Workspace, Teams, Slack, SharePoint, and OneDrive.
AI-driven phishing prevention
Blocks sophisticated social engineering attacks and zero-day phishing attempts.
Malware & Ransomware Defense
SandBlast technology emulates threats and extracts malicious content, ensuring safe delivery without disrupting productivity.
Account takeover protection (ATO)
Uses machine learning to detect suspicious logins, compromised devices, and unusual user behavior, blocking unauthorized access
Single License
Covers both email and collaboration tools, streamlining management and reducing total cost of ownership (TCO).
Unified Dashboard
Provides actionable insights, detailed reporting, and full visibility across all security functions for simplified administration.
Incomming Email
phishing Scan
Malware Defense
Sercure Mail
Harmony Protects What Others Miss
– Shadow IT Risks
Employees often use cloud apps and services without IT approval – this is known as Shadow IT. While convenient, it creates blind spots that can put sensitive business data at risk.
With Check Point Harmony’s Shadow IT feature, you gain full visibility and control:
-
Detect Unapproved Apps – Automatically identifies when employees use cloud apps outside company policy.
-
Risk Analysis – Rates the security level of each app so you can focus on the most critical risks.
-
Central Dashboard – Provides clear insights into which apps are being used, by whom, and how often.
-
Policy Enforcement – Approve safe apps or block risky ones to protect your data and maintain compliance
ThreatCloud Integration
Stay ahead of cyber threats with real-time intelligence from billions of indicators. Detect phishing, malware, and zero-day attacks instantly, keeping your email and collaboration platforms secure.
API Based Integration
Seamlessly deploy advanced email security into your existing environment. Fast, disruption-free, and fully protected against phishing, malware, and cyber threats.
Get Industry-Leading Phishing Protection with Vays Infotech
Check Point Harmony transformed our email security. The setup was seamless, and threats are blocked in real time.
Defend Your Enterprise Email with Next-Gen Security
Proofpoint is a leading cybersecurity platform that protects people, data, and brands from advanced threats. Focused on email security solutions bangalore —the #1 entry point for cyberattacks—it defends against phishing, ransomware, malware, and business email compromise.
Beyond email, Proofpoint secures cloud apps, social media, and collaboration tools, while offering threat intelligence, user training, and compliance features. Trusted by businesses worldwide, it delivers enterprise-grade protection against today’s most sophisticated cyber threats.
Advanced Features That Make Proofpoint Email Security Stand Out
Protect your organization with AI-powered threat detection, email archiving & continuity, cloud and collaboration security, real-time threat intelligence, user awareness training, and compliance support — all in one trusted platform..
URL Defense
Rewrites and inspects links at click-time
Attachment Defense
Sandboxing to block malicious files
Advanced BEC Defense (Supernova AI engine)
Detects impersonation and fraud emails

Email Encryption
Auto-encrypts based on policy triggers
Data Loss Prevention (DLP)
Prevents exposure of sensitive data (PII, PCI, HIPAA)

Why Choose Proofpoint Email Security?
– Global leader in email protection
– Al-driven threat detection
– Compliant & secure long-term retention
– Proactive business continuity measures
Frequently Asked Questions
Why Vays?
At Vays, we specialize in delivering an extensive range of IT support services across major cities in India. Our focus areas include network security, firewall management, and cybersecurity.
Our offerings comprehensively cover the protection of networks, operating systems, hardware, applications, and cloud environments. With meticulous attention to detail, we actively ensure that businesses have robust security measures in place to safeguard their critical assets from cyber threats and vulnerabilities.
Our dedicated team takes pride in providing a human touch to our services, prioritizing the specific needs and concerns of each client.


Customized Solutions
Every business is unique, and so are its network security needs. Recognizing this, we don’t believe in a one-size-fits-all approach. Instead, we take the time to understand your specific business operations, infrastructure, and potential threats to provide a customized firewall solution.

Employee Training
We equip your team with the necessary knowledge to maintain network security and react to potential threats. This includes teaching them best practices for secure network use, and showing them how to respond effectively in case of a potential security incident.

Save costs
Our network security and cyber security professionals provide businesses with specialized skills and knowledge, allowing them to focus on their core operations. This enhances overall productivity and efficiency. With our dedicated professionals safeguarding networks and systems, businesses can confidently pursue success.

Expertise
Our team’s deep knowledge in Firewall implementation ensures maximum protection. Our professionals possess specialized skills and knowledge, enabling businesses to prioritize core operations. This strategic approach enhances productivity and efficiency as dedicated experts handle critical security aspects