
by vsjawahar | Jan 31, 2025 | AI (Artificial Intelligence), Application Management
What is DeepSeek? DeepSeek is an open-source large language model (LLM) designed for natural language processing (NLP) tasks, similar to OpenAI’s ChatGPT. Developed by DeepSeek AI, it aims to provide high-performance AI capabilities with transparency and...

by vsjawahar | Jan 29, 2025 | IT Networking, Wireless Networking
The essential solutions for a secured networking in an enterprise include: Firewalls: Next-Generation Firewall (NGFW) is an essential component, especially for businesses with remote workers and high security demands. NGFWs provide site-to-site and remote access VPNs...

by vsjawahar | Jan 29, 2025 | IT Networking, Meraki AP's, Wi-Fi 7, Wireless Networking
Selecting the right access point is crucial for establishing a fast, secure, and reliable wireless network. Cisco Meraki provides a variety of options, but today we’ll focus on two prominent models—the Meraki MR44 and Meraki MR57. Both models feature advanced...
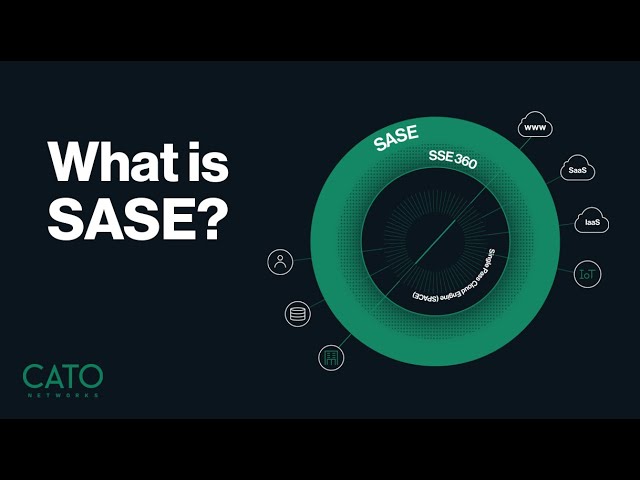
by vsjawahar | Feb 9, 2024 | Cybersecurity, Network Security
Introducing SASE ( Secure Access Service Edge) SASE, or Secure Access Service Edge, is a cybersecurity strategy that increases people’s flexibility and safety when using company data and apps from any location. It employs a “trust no one”...

by vsjawahar | Feb 9, 2024 | Cybersecurity, Network Security
Introduction to ZTNA (Zero Trust Network Access) Protecting our digital information is critical. Traditional network security measures, such as virtual barriers, are no longer as effective as they once were. Consider a scenario in which you can’t simply...






